Security Summit Keynote
Security and Boundaries
James Bottomley
CTO of Server Virtualization

About Me
Kernel Developer
- SCSI Subsystem Maintainer
- PA-RISC architecture Maintainer
Linux Foundation TAB
Would love to give a detailed talk on this
Unfortunately, Matthew Garret got there before me
Instead, lets talk about some of the general problems raised by UEFI
Secure boot
Key problem is security boundary
Also known as who trusts what
UEFI gives absolute control to platform owner. No trust to OS
But OS wants to make use of UEFI root of trust
Linux solves this by using SHIM to transition to OS root of trust
Basically, we subvert the UEFI root of trust
So, how should we do this properly?
Boundaries of Trust
First problem is "Should trust be absolute?"
That is the UEFI Model ... OS is subservient to UEFI root of trust
Problem also exists in modern Operating Systems
Consider networking
In the old days, OS controlled the network
Today, thanks to untrusted hypervisors, Users can access entire network L2
layer
Users could only create sockets with ports > 1024
Boundary of trust has shifted
Aside about Containers
Containers are no less nor more secure than hypervisors
Arguing over which is "more secure" is like arguing where the holes in a
colendar should be
The only thing you can bet on is that containers shift the security
boundary
Coping with a shifting security boundary means changing the way we trust
things
Prediction vs Trust vs Verification
In Law enforcement, Predictive is considered Orwellian
Can't bang someone up just becuase you think they're going to commit a
crime
In computing too, predictive models are currently too flawed.
Still get my email blocked because my netblock contains machines bought
by spammers.
So if prediction doesn't work, where is the boundary between trust and
verification?
Prevention works
Locks prevent theft
Atmospheric sedation would largely prevent crimes of violence
One is prudent, one damages utility.
Security is about finding the balance between utility and prevention
Also: Consider whom you're serving
I want security to serve me, not some admin in the IT dungeon
Password rotation policies biggest source of security problems in IT.
It's like the IT department is pushing it's problem (logging and
verification) on to me (password rotation)
Ironically, this is one we can blame Microsoft for
Password rotation is a recommended part of Active Directory security
policies
Need to make security more easily useful to the average person
Firefox password manager is a brillant example
I can actually remember strings of random numbers digits and punctuation
Well, about five of them, anyway
But this doesn't scale to hundreds
Which is the number of web accounts I have
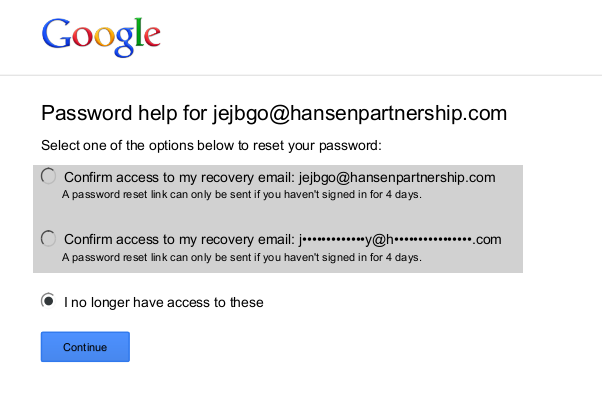
2 Factor Authentication, help or hindrance?
Main problem is lack of interoperability across authentication domains
2 Factor vs security recovery
Recovery has to be simple (or at least possible)
Linux Security
In April, no Significant Vulnerability Problem
In May, not so much
Linux TTY
privilege escalation
Big Oops
Buffer overflows again
is C to blame?
Always have a plan B
The entire security of the internet depends on two unsolved mathematical
problems
- Discrete Logarithms
- Prime Factorisation
On the day either of these is solved, our internet security systems: SSL,
TSL, go up in smoke
So what's our plan B?
If the boundary moves, embrace it
Security Systems always need to consider the consequences of
implementation
Who are you serving (user, administrator, site ...)
And who should you be serving
Assisting the enterprise (or the administrator) can lead to loss of
security
Best security helps the willing consumer do something they want to do
Strong verification is essential
But easy recovery in case of verification failure is also essential